
XymbolicPH InfoSec Management System (XIMS)
is a set of information security technology policies and procedures for systematically managing an organization's sensitive data. The goal of XIMS is to minimize risk and ensure business continuity by proactively limiting the impact of a security breach.
XIMS typically addresses employee behavior and processes, as well as data and technology. It can be targeted toward a particular type of data, such as customer data, or it can be implemented in a comprehensive way that becomes part of the company's culture.
Protects sensitive data
XIMS protects all types of our proprietary information assets, whether they're paper-based, preserved digitally, or reside in the cloud. These assets can include personal data, intellectual property, financial data, customer data, and other data we entrusted to other companies through third parties.
Regulatory compliance
XIMS helps our company meet all regulatory compliance and contractual requirements and provides a better grasp on the legalities surrounding information systems. Since violations of legal regulations come with hefty fines, it can be beneficial for highly regulated industries with critical infrastructure like us.
Provides business continuity
automatically increase their level of defense against threats. XIMS reduces the number of security incidents, such as cyber attacks, resulting in fewer disruptions and less downtime, which are important factors for maintaining business continuity.
Enhances company culture
XIMS provides approach for security and asset management throughout our organization that isn't limited to IT security. This encourages all our employees to understand the risks tied to information assets and adopt security best practices as part of their daily routines.
Reduces costs
XIMS enables our organizations to prioritize the highest-risk assets to prevent indiscriminate spending on unneeded defenses and provide a focused approach toward securing them. This structured approach, along with less downtime due to a reduction in security incidents, significantly cuts an organization's total spending.
Adapts to emerging threats
Security threats are constantly evolving. XIMS helps our organizations prepare and adapt to new threats and the continuously changing demands of the security landscape.
Our Security Controls
We are in good company.






POLICY STATEMENT
XIMS recognizes the additional security hazards posed by network systems and wishes to reduce these threats wherever possible.
The policy restricts the transfer of confidential information over unprotected communication links, whether within the organization’s private network or via a public network.
The confidentiality and integrity of data stored on company computer systems must be protected by access controls to ensure that only authorized employees have access. This access shall be restricted to only those capabilities that are appropriate to each employee’s job duties. This access is controlled by XIMS identity and access management.
PROCEDURES
Each employee will be given a unique company user access identity once a request has been received from the HR Department.
The employee will also be given a unique email address for use with the company’s email system.
Each employee shall be responsible for all computer transactions that are made with his or her account ID and password.
Further, those in financial, HR, or any role that could contain confidential data should lock the screen of their computer when leaving a workstation for an extended period.
Managers and supervisors should notify the HR department promptly whenever an employee leaves the company or transfers to another department, so that his or her identity access can be terminated.
Involuntary terminations must be reported concurrent with the termination.
Managers should ensure the level of user access is appropriate for the work being undertaken and should not compromise the integrity of XIMS.
XIMS Identity and Access Management.
Managed and protected by Microsoft Entra ID.
XIMS safeguard our organization with a cloud identity and access management solution that connects employees, customers, and partners to their apps, devices, and data.
Secure adaptive access
XIMS protect access to our resources and data using strong authentication and risk-based adaptive access policies without compromising the user experience.
Seamless user experiences
XIMS provide a fast, easy sign-in experience across our multi-cloud environment to keep our users productive, reduce time spent managing passwords, and increase productivity.
Unified identity management
XIMS manage all our identities and access to all our applications in a central location, whether they’re in the cloud or on-premises, to improve visibility and control.

POLICY STATEMENT
XIMS is committed to the correct use of passwords as a means of controlling access to information contained on the networks and business systems.
Passwords and multi-factor authentication are enforced for all users accessing this information and are required to be changed on a periodic basis. It is the responsibility of every individual to ensure password information is secure and never divulged.
PROCEDURES
Access to all company infrastructure systems is controlled via your network login. Associated with your login name is your password. Therefore, it is vital that your password is never disclosed. The following procedures will ensure maximum security:
Users should keep their passwords and secrets and not allow anyone else to use them or know them.
Passwords will be required to be changed every 90 days and frequency will be evaluated annually. The last six used passwords are blocked from being reused.
Passwords should have a minimum length of 8 characters to deter unauthorized attempts to discover them by trial and error.For some reason, passwords should not be meaningful words but should be random permutations of letters, numbers, and special characters.
Users should not select guessable, predictable words such as their name, nickname, job title, or anything else that can be easily guessed. Guessable or “weak” passwords will be blocked by the system.
Users should never leave a computer logged in and unattended. Users who leave their computers unattended must be on lockout. Passwords are required when the device returns from idle states. If assistance is needed, contact the XIMS Department.
Users or laptop computers who are in financial, HR, or any other role that would be responsible for confidential data must use hardware-level device security and storage encryption. Contact the XIMS Department for assistance.
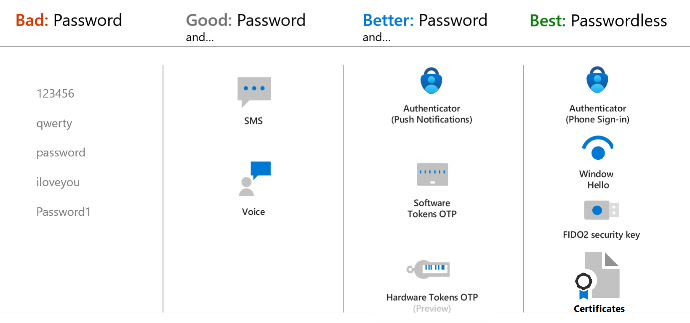
Authentication methods used by XIMS
Microsoft Entra multi-factor authentication adds additional security over only using a password when a user signs in. The user can be prompted for additional forms of authentication, such as to respond to a push notification, enter a code from a software or hardware token, or respond to a text message or phone call.
SMS - SMS-based authentication lets users sign-in without providing, or even knowing, their user name and password. After their account is created by an identity administrator, they can enter their phone number at the sign-in prompt. They receive an SMS authentication code that they can provide to complete the sign-in. This authentication method simplifies access to applications and services, especially for Frontline workers.
Voice Call - With phone call verification during SSPR or Microsoft Entra multifactor authentication, an automated voice call is made to the phone number registered by the user. To complete the sign-in process, the user is prompted to press # on their keypad.
MS Authenticator app - Users may receive a notification through the mobile app for them to approve or deny, or use the Authenticator app to generate an OATH verification code that can be entered in a sign-in interface. If you enable both a notification and verification code, users who register the Authenticator app can use either method to verify their identity.
POLICY STATEMENT
XIMS is committed to using the internet access for business purposes, it must ensure that suitable controls are in place to prevent security breaches or negative consequences. The networks used for the Internet are not secure, and any communications sent by this means could be accessed or modified by unauthorized individuals.
There are also threats from obtaining information from the internet, with virus attachments being the most common. Consequently, we must adopt procedures that minimize the risk of using the internet and follow good practices in the way individuals behave and the internet sites that they visit.
We have established our internet access for specific business purposes, and personal use is restricted. Where materials are obtained from the internet. Ensure that any copyright restrictions are obeyed and that virus protection procedures are followed. Where material we own is published, ensure that it carries our copyright markers.
Internet connectivity presents the company with new risks that must be addressed to safeguard the facility’s vital information assets. These risks include:
Access to the Internet by personnel that is inconsistent with Business needs result in the misuse of resources. These activities may adversely affect productivity due to time spent using or "surfing" the Internet. Additionally, the company may face a loss of reputation and possible legal action through other types of misuse.
All information found on the Internet should be considered suspect until confirmed by another reliable source. There is no quality control process on the Internet, and a considerable amount of its information is outdated or inaccurate.
Access to the Internet will be provided to users to support business activities and only on an as needed basis to perform their jobs and professional roles.
PROCEDURES
The Internet usage policy applies to all roles (individuals working for the company, including permanent full-time and part-time employees, contract workers, temporary agency workers, business partners, and vendors) who access the Internet through computing or networking resources. The XIMS Internet users are expected to be familiar with and comply with this policy, and they are also required to use their common sense and exercise their good judgment while using Internet services.
Access to the Internet will be approved and provided only if reasonable business needs are identified. Internet services will be granted based on an employee’s current job responsibilities. If an employee moves to another business unit or changes job functions, a new Internet access request must be submitted within 5 days.
User Internet access requirements will be reviewed periodically by XIMS to ensure that continuing needs exist.
Internet usage is granted for the sole purpose of supporting business activities necessary to carry out job functions. All users must follow the corporate principles regarding resource usage and exercise good judgment when using the Internet. Questions can be addressed to XIMS.
Acceptable use of the Internet for performing job functions might include:
- Communication between employees and non-employees for business transaction purposes.
- IT technical support downloads software upgrades and patches.
- Review of possible vendor web sites for product information.
- Reference regulatory or technical information.
- Research.
Using company computer resources to access the Internet for personal purposes without approval from the user’s department manager or supervisor and XIMS may be considered cause for disciplinary action up to and including termination.
All users of the Internet should be aware that the company network creates an audit log reflecting requests for service, both inbound and outbound, which is periodically reviewed.
Internet access will be discontinued upon termination of employee, completion of contract, end of service of non-employee, or disciplinary action arising from violation of this policy. In the case of a change in job function and/or transfer, the original access code will be discontinued and only reissued if necessary and a new request for access is approved.
Prohibited use of third-party email providers and cloud storage services. Company email systems are limited to the use of company email systems and company storage services only. Third-party email providers and cloud storage service providers are strictly not allowed.
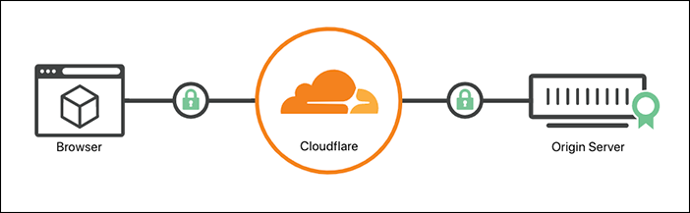
XIMS uses SSL/TLS Full Encryption Mode.
An SSL/TLS certificate is what enables websites and applications to establish secure connections. With SSL/TLS, a client, such as a browser, can verify the authenticity and integrity of the server it is connecting with and use encryption to exchange information.
We enable Cloudflare SS/TLS certificates to encrypt our web traffic and prevent data theft.
POLICY STATEMENT
XIMS is committed to the use of authorized software only within its computer systems. Only XIMS approved software should be utilized within the organization. Any software other than the XIMS approved requires the authorization of a department manager along with the Chief Information Officer (CIO). Proof of purchase must be provided prior to approval.
XIMS strongly supports strict adherence to software vendors’ license agreements. When at work or when company computing or networking resources are employed, copying software in a manner not consistent with the vendor’s license is strictly forbidden. Questions regarding lawful versus unlawful copying should be referred to XIMS for review or to request a ruling from the Legal Department before any copying is done.
PROCEDURES
It is the responsibility of both the individual and management to ensure only authorized software is used on company endpoints. Software that a user may require in the normal course of their duties can be acquired through the normal procurement procedure.
The company has the capability of checking the software being used on all networked and stand-alone PCs and will periodically check to ensure the user has not attempted to load and use any unauthorized software. The results of these compliance audits will be reported to local management. Any breaches in the use of legal software will be immediately reported to local management.
List of approved software:
- Windows 10/11 Pro/Enterprise
- Microsoft 365 Office Apps Enterprise
- Browser Application (Google Chrome, Edge, Firefox)
- Messenger/Conferencing App (Viber, WeChat, WhatsApp, Zoom)
- Printer/Scanner Drivers & Application
All other software will be considered unauthorized and will not be allowed.
No employee may use company resources and internet access to download or distribute pirated software or data.
POLICY STATEMENT
XIMS is committed to providing secure and reliable remote support and control capabilities to users when working away from their normal place of work.
PROCEDURES
No remote support to the computer network will be permitted unless it is authorized by the employee’s manager and the Chief Information Office (CIO). The XIMS will determine the most secure method for remote support.
It is the user's responsibility to ensure their ID or password is never disclosed or given out so that a third party could either inadvertently or maliciously enter the company network or resources.
XIMS Remote Work Solutions uses TeamViewer Tensor.
TeamViewer Tensor is a cloud-based enterprise connectivity platform that enables large-scale IT management framework deployments quickly and easily. The most agile and secure remote work solutions for enterprises.
TeamViewer is proud to be the only Microsoft Intune partner to offer seamless and secure remote support and remote control capabilities directly from the Intune dashboard. In just a few clicks, XIMS can activate an automatic TeamViewer rollout on all Intune-managed devices.
And since TeamViewer is a GDPR-compliant, end-to-end encrypted solution, our corporate data is protected.
With XIMS remote access and control built right into the Intune dashboard, it’s easy to troubleshoot and administer corporate-owned devices from anywhere. That means faster resolution times for support issues and less downtime for corporate users on their devices, saving our organization time and money.

POLICY STATEMENT
XIMS is committed to the security and access of company information. Any attempted breach will be recorded, and appropriate disciplinary action will be taken. The XIMS Department is the only group authorized to monitor network services.
Users should consider their Internet activities to be periodically monitored and limit their activities accordingly.
The XIMS reserves the right to examine e-mail, personal file directories, web access, and other information stored on company computers at any time and without notice. This examination ensures compliance with internal policies and assists with the management of company information systems.
PROCEDURES
XIMS logs and audits the use of its computer systems, including internet access and data. All usage is recorded and regularly audited. The purposes of logging, auditing, monitoring, and recording are to:
- Ensure the effective operation of the company’s systems and to maintain the system security.
- Investigate and detect unauthorized use of the system in breach of company policies.
- Investigate allegations of misconduct, breach of contract, criminal offense, or fraud by the user or third party.
- The XIMS Department will check these logs on a regular basis, and where a breach of policy, security breach, or attempted security breach is suspected, the matter will be investigated and brought to the attention of HR or senior management.
Users must not place company material (examples: internal memos, press releases, product or usage information, documentation, etc.) on any mailing list, public news group, or such service. Any posting of materials must be approved by the employee’s manager or supervisor and the public relations department and will be placed by an authorized individual.

XIMS Endpoint Management
Managed and protected by Microsoft Endpoint Manager.
Microsoft Endpoint Manager (MEM) is a cloud-based solution that is designed to address the challenges associated with deploying, managing, and securing devices in an enterprise. This includes servers, PCs, and mobile devices.
Microsoft Intune reports allow us to more effectively and proactively monitor the health and activity of our endpoints across our organization, and they also provide other reporting data across Intune. We see reports about device compliance, device health, and device trends. In addition, we can create custom reports to obtain more specific data.
POLICY STATEMENT
XIMS is committed to the protection of its information by means of secure backups of application systems, software, and data.
PROCEDURES
All information that may be needed later must be protected by taking and keeping a secure copy of this information. This is what is known as a backup.
Backups must always be secured when un-attended so that sensitive information cannot be compromised.
The last backup taken within a significant time in a processing cycle is to be kept off-site in a secure location.
Backup media should be clearly labeled.
Periodic attempts to restore information from backup files should be performed to ensure information is usable and readable.
All information stored on central/network file servers should be backup on a daily incremental and weekly full.
Where information is stored locally on a users own hard drive. All users data are stored on company onedrive so that data is backup.
All laptop users must ensure that the data held on the laptop is regularly backup to company onedrive real-time.
XIMS Real-Time User Data Backup
Managed and protected by Microsoft OneDrive for Business.
With OneDrive for Business, formally SkyDrive Pro, organizations can get started with a robust, full-featured and intuitive file sync and share service that benefits from deep integration with Office.
OneDrive is designed to do both sync and backup. It will automatically save a file copy on your local device and in the cloud. This allows you to have a live backup that you can access from anywhere. You can also set it up to only back up specific folders

POLICY STATEMENT
XIMS is committed to providing cyber threat protection on all its computer hardware to maximize the risk to the company from any cyber threats.
Cyber threat protection (CTP) refers to a category of security solutions that defend against sophisticated malware or hacking-based attacks targeting sensitive data. Cyber threat protection solutions can be available as software or as managed services. CTP solutions can differ in approaches and components, but most include some combination of endpoint agents, network devices, email gateways, malware protection systems, and a centralized management console to correlate alerts and manage defenses.
The primary purpose of threat protection policy is the ability to prevent, detect, and respond to new and sophisticated attacks that continue to become increasingly targeted, stealthy, and persistent, and this policy solution takes a proactive approach to security by identifying and eliminating advanced threats before data is compromised.
The three primary goals of advanced threat protection are: early detection (detecting potential threats before they can access critical data or breach systems), adequate protection (the ability to defend against detected threats swiftly), and response (the ability to mitigate threats and respond to security incidents). To achieve these goals, cyber threat protection services and solutions must offer several components and functions for comprehensive CTP:
- Real-time visibility: without continuous monitoring and real-time visibility, threats are often detected too late. When damage is already done, response can be tremendously costly in terms of both resource utilization and reputation damage.
- Context: For true security effectiveness, threat alerts must contain context to allow security teams to effectively prioritize threats and organize responses.
- Data awareness: It is impossible to determine threats truly capable of causing harm without first having a deep understanding of enterprise data, its sensitivity, value, and other factors that contribute to the formulation of an appropriate response.
When a threat is detected, further analysis may be required. Security services offering CTP typically handle threat analysis, enabling enterprises to conduct business as usual while continuous monitoring, threat analysis, and response occurs behind the scenes. Threats are typically prioritized by potential damage and the classification or sensitivity of the data at risk. Cyber threat protection should address three key areas:
PROCEDURES
XIMS licenses endpoint detection and response software for use on all devices within the company. These include firewalls, emails, internet access, file servers, and personal computers.
As part of the procedures, XIMS automatically receive updates to the endpoint detection and response on a regular basis or when new threats are detected. This is automatically updated on all devices except personal computers that are not currently attached to the network, in which case it is the responsibility of everyone to ensure they keep The PC was loaded with the latest version of EDR software.
Laptop Computer users should take extra care to ensure they have the latest EDR software, as they are always directly connected to the network. Any on the notification of the presence of the threats should be immediately reported to XIMS.
POLICY STATEMENT
Protection of information assets is the responsibility of XIMS. The owner of a given information asset will be the end-user group or business unit that has the most significant interest in the use of the asset. XIMS is accountable for ensuring that appropriate security and integrity controls are in place.
PROCEDURES
Data owner responsibilities includes:
- Assessing information assets to determine the confidential or otherwise sensitive nature of the asset.
- Identifying and evaluating access and security requirements for information assets and specifying authorizations applicable to end-users; access must be consistent with applicable laws and contractual obligations; access should follow the principle of least privilege.”
- Ensuring that the certification of access privileges to information assets is performed annually.
- Verifying that the frequency of system and data file backups and off-site storage procedures are adequate to ensure a timely recovery. In the event of a major hardware or software failure and in a manner consistent with legal and regulatory requirements.
- Key systems are to be inventoried annually by the data owners.
The acquisition, storage, and dissemination of data that is illegal, pornographic, or that negatively depicts race, sex, or creed is specifically prohibited.
XIMS also prohibits the conduct of a business enterprise, political activity, engaging in any form of intelligence collection from our facilities, engaging in fraudulent activities, or knowingly disseminating false or otherwise libelous materials.
Other activities that are strictly prohibited include, but are not limited to:
- Accessing company information that is not within the scope of one’s work. This includes the unauthorized reading of customer account information, unauthorized access to personnel files information, and accessing information that is not needed for the proper execution of job functions.
- Misusing, disclosing without proper authorization, or altering customer or personnel information. This includes making unauthorized changes to a personnel file or sharing electronic customer or personnel data with unauthorized personnel.
- Deliberate pointing or hyper-linking of company Web sites to other Internet or WWW sites whose content may be inconsistent with or in violation of the aims or policies of the company.
- Any conduct that would constitute or encourage a criminal offense, lead to civil liability, or otherwise violate any regulations, local, state, national, or international law, including without limitations to export control laws and regulations,.
- Use, transmission, duplication, or voluntary receipt of material that infringes on the copyrights, trademarks, trade secrets, or patent rights of any person or organization. Assume that all materials on the Internet are copyrighted and/or patented unless specific notices state otherwise.

XIMS complies with the Data Privacy Act
10173, also known as the Data Privacy Act of 2012. It was signed into law by President Benigno Aquino III on August 15, 2012. The aim is to protect personal data in information and communications systems, both in the in the private and government sectors.
Data privacy is the protection of personal data from those who should not have access to it and the ability of individuals to determine who can access their personal information.
Protection of Personal Information: Data privacy safeguards individuals' personal information from unauthorized access, ensuring that sensitive data such as social security numbers, financial records, and health information remains secure.
POLICY STATEMENT
The purpose of this policy is to provide standards and rules of behavior for the use of personally owned devices (PODs) like smart phones and/or tablets by employees to access company network resources and/or services. Access to and continued use is granted on the condition that each user reads, signs, respects, and follows the policies concerning the use of these resources and/or services.
Expectation of Privacy will respect the privacy of your personal device and will only request access to the device by XIMS to implement security controls or to respond to legitimate discovery requests arising out of administrative, civil, or criminal proceedings.
PROCEDURES
Devices must be presented to the XIMS and/or Representative for proper job provisioning and configuration of standard apps, such as browsers, office productivity software, and security tools, before they can access the network.
To prevent unauthorized access, devices must be password protected using the features of the device, and a strong password is required to access the company network.
The device must lock itself with a password or PIN if it is idle for five minutes.
Smartphones and tablets that are not on the company’s list of supported devices are not allowed to connect to the network.
Employees’ access to company data is limited based on user profiles defined by the XIMS and automatically enforced.
The employee’s device may be remotely wiped if:
- The device is lost or stolen.
- The employee terminates his or her employment.
- The XIMS detects a data or policy breach, a virus, or a similar threat to the security of the company’s data and technology infrastructure.
While the XIMS will take every precaution to prevent the employee’s personal data from being lost in the event it must remote wipe a device, it is the employee’s responsibility to take additional precautions, such as backing up email, contacts, etc.
The company reserves the right to disconnect devices or disable services without notification.
Lost or stolen devices must be reported to XIMS within 24 hours. Employees are responsible for notifying their mobile carrier immediately upon the loss of a device. The employee is expected to always use his or her devices in an ethical manner and adhere to the company’s acceptable use policy as outlined above.
The employee is personally liable for all costs associated with his or her device.
The employee assumes full liability for risks including, but not limited to, the partial or complete loss of company and personal data due to an operating system crash, errors, bugs, viruses, malware, and/or other software or hardware failures, or programming errors that render the device unusable.
reserves the right to take appropriate disciplinary action up to and including termination for noncompliance with this policy.
XIMS Devices Compliance Policies
Managed and protected by Microsoft Intune Endpoint Management.
Password
- Require a password to unlock devices.
- Block devices from using simple passwords.
- Password complexity requires combinations of digits, lowercase, uppercase, and special characters.
- The minimum password length is enabled.
- Maximum minutes of inactivity before a password is required.
- Password expiration days after the device password must be changed are enabled.
- The number of previous passwords to prevent reuse is enabled.
Encryption
- Require encryption of data storage on devices.
- Microsoft Attestation service evaluation settings require the following protective measure settings enabled at boot time: Bitlocker, Secure Boot, and Code Integrity.
Device Security
- Require a firewall to be on and monitoring.
- Require Trusted Platform Module (TPM) to be present.
- It requires an antivirus and anti-spyware solution registered with the Windows defender security center to be on and monitored.
Defender
- It requires the Microsoft Defender service to be enabled.
- Require Microsoft Defender security intelligence to be up-to-date.
- Require real-time protection prompts for known malware detection.
Android/iOS
- Prevent rooted and jail-broken devices from having corporate access.
- Check if Google Play services or the Apple Store are installed and enabled.
- The security provider must be up-to-date.
- Block apps from unknown sources.
- Block USB debugging on devices.

Business Continuity Plan (BCP)
A business continuity plan is a document that explains the actions you should take before, during, and after unexpected events and situations. It is designed to help you identify, prevent, or reduce risks where possible. Prepare for risks that are out of your control.
The Business Continuity Plan (BCP) for Xymbolic IT Solution Provider Corp. serves as a comprehensive framework to ensure the company's resilience and continuity in the face of unexpected disruptions or disasters. Its primary purpose is safeguarding critical business operations, minimizing downtime, and enabling rapid recovery. The BCP emphasizes proactive preparedness, risk mitigation, and effective response strategies to protect the reputation, assets, and customer trust of Xymbolic as the premier IT store in Olongapo City.
PURPOSE
The Business Continuity Plan (BCP) for Xymbolic IT Solution Provider Corp. serves as a comprehensive framework to ensure the company's resilience and continuity in the face of unexpected disruptions or disasters. Its primary purpose is safeguarding critical business operations, minimizing downtime, and enabling rapid recovery. The BCP emphasizes proactive preparedness, risk mitigation, and effective response strategies to protect the reputation, assets, and customer trust of Xymbolic as the premier IT store in Olongapo City.
SCOPE
The BCP encompasses all facets of Xymbolic IT Solution Provider Corp. operations, covering both its main location at # 16 Mt. Apo Street, East Tapinac, Olongapo City, as well as the branch located in Ortigas, Pasig City. It includes the preservation of critical business functions, information systems, infrastructure, personnel safety, and communication protocols. The plan extends to cover potential disruptions caused by natural disasters, cyber incidents, hardware failures, supply chain interruptions, and any other threats that may arise.
KEY OBJECTIVES
- Continuity of Operations: Ensure the uninterrupted delivery of products and services, guaranteeing that customers continue to receive exceptional IT solutions and support, even in the face of adversity.
- Minimize Downtime: Reduce the impact of disruptions on business operations by implementing measures to swiftly recover IT systems, hardware, and infrastructure.
- Data Protection and Recovery: Establish robust data backup and recovery mechanisms to safeguard critical information and prevent data loss.
- Risk Mitigation: Identify potential risks and vulnerabilities, and proactively implement measures to mitigate these risks, thereby enhancing the company's overall resilience.
- Resource Management: Allocate and optimize resources efficiently to facilitate the execution of the BCP effectively.
- Personnel Safety and Welfare: Prioritize the safety and well-being of Xymbolic's employees, ensuring clear communication channels for their security during a crisis.
- Stakeholder Communication: Establish a robust communication plan to keep customers, employees, vendors, and relevant authorities informed about the situation, progress, and recovery efforts.
- Testing and Training: Regularly conduct drills and exercises to evaluate the efficacy of the BCP and provide training to employees to familiarize them with their roles and responsibilities during an incident.
- Compliance and Governance: Ensure that the BCP aligns with industry standards, regulatory requirements, and best practices related to business continuity and data protection.
CRITICAL IMPORTANCE OF BUSINESS CONTINUITY
As the premier IT store in Olongapo City since 2018, Xymbolic IT Solution Provider Inc. plays a crucial role in providing cutting-edge technologies and support to individuals and businesses alike. The critical importance of business continuity cannot be overstated, as any disruption to Xymbolic's operations could not only result in financial losses but also erode the trust and confidence that customers have placed in the brand.
By proactively implementing a robust BCP, Xymbolic demonstrates its commitment to delivering uninterrupted services, ensuring data security, and safeguarding the interests of its stakeholders. In the event of unforeseen events, the BCP will enable Xymbolic to respond swiftly and efficiently, maintaining its status as the preferred IT solution provider and upholding its reputation for reliability and customer satisfaction in Olongapo City and beyond.
BACKGROUND OF XYMBOLIC IT SOLUTUONS PROVIDER INCORPORATION
Xymbolic IT Solution Provider Inc has emerged as the leading IT services and business solution provider in the Philippines since its inception in 2016. Founded on a vision of empowering businesses and individuals with cutting-edge technology, Xymbolic has rapidly established itself as a trusted brand in the IT industry.
LOCATIONS IN OLONGAPO CITY AND PASIG CITY
Xymbolic IT Solution Provider Inc has emerged as the leading IT services and business solution provider in the Philippines since its inception in 2016. Founded on a vision of empowering businesses and individuals with cutting-edge technology, Xymbolic has rapidly established itself as a trusted brand in the IT industry.
SERVICES PROVIDED
Xymbolic IT Solution Provider Inc has emerged as the leading IT services and business solution provider in the Philippines since its inception in 2016. Founded on a vision of empowering businesses and individuals with cutting-edge technology, Xymbolic has rapidly established itself as a trusted brand in the IT industry.
- IT Consulting: Expert consultants at Xymbolic assess clients' existing IT infrastructure and recommend tailored solutions to optimize efficiency, reduce costs, and align technology with business objectives.
- Hardware Solutions: Xymbolic offers a wide selection of top-quality computer hardware, including laptops, desktops, servers, networking equipment, and peripherals, sourced from reputable brands.
- Software Solutions: The company provides licensed software solutions for diverse purposes, such as operating systems, productivity suites, security software, and custom software development.
- Managed IT Services: Xymbolic offers comprehensive managed IT services, including system monitoring, maintenance, remote support, and IT security management to ensure smooth operations and data protection.
- Cloud Services: Recognizing the importance of cloud computing, Xymbolic assists clients in transitioning to cloud-based solutions for enhanced scalability, data accessibility, and cost-effectiveness.
- Cybersecurity Solutions: The company focuses on safeguarding clients' digital assets by offering robust cybersecurity solutions, including firewall installation, data encryption, and vulnerability assessments.
- IT Training and Workshops: Xymbolic provides IT training sessions and workshops to empower clients and their employees with the necessary skills to harness the full potential of technology.
NEED FOR A BCP AND COMMITMENT OF MANAGEMENT
The implementation of a Business Continuity Plan (BCP) is of paramount importance for Xymbolic IT Solution Provider Inc due to several compelling reasons:
- Ensuring Uninterrupted Operations: As the leading IT services provider, Xymbolic's clients rely on its seamless and consistent services. A BCP is vital to maintain business continuity during unexpected disruptions, ensuring clients receive uninterrupted support.
- Mitigating Risks: The IT industry faces a wide array of risks, including cyber threats, natural disasters, and hardware failures. A BCP enables Xymbolic to proactively identify and mitigate these risks, minimizing potential negative impacts.
- Ensuring Uninterrupted Operations: As the leading IT services provider, Xymbolic's clients rely on its seamless and consistent services. A BCP is vital to maintain business continuity during unexpected disruptions, ensuring clients receive uninterrupted support.
- Mitigating Risks: The IT industry faces a wide array of risks, including cyber threats, natural disasters, and hardware failures. A BCP enables Xymbolic to proactively identify and mitigate these risks, minimizing potential negative impacts.
The commitment of Xymbolic IT Solution Provider Inc's management to implementing a BCP is resolute. They understand that proactive preparedness is essential for the long-term sustainability of the business and the satisfaction of its clientele. Management is dedicated to investing the necessary resources, conducting regular drills, and engaging the entire organization to ensure the successful implementation and continuous improvement of the BCP. By prioritizing business continuity, Xymbolic remains steadfast in its mission to provide unrivaled IT services and solutions to clients in Olongapo City, Pasig City, and beyond.
The Business Impact Analysis (BIA) is a crucial step in developing a comprehensive Business Continuity Plan (BCP) for Xymbolic IT Solution Provider Inc. It helps identify critical business processes, IT systems, and resources, and assesses the potential impact of disruptions on the organization. Let's conduct a thorough BIA to ensure the BCP is tailored to address the specific needs and vulnerabilities of Xymbolic.
IDENTIFY CRITICAL BUSINESS PROCESSES
- Sales and Customer Service: The process of handling customer inquiries, sales, and after-sales support is vital to maintain customer satisfaction and business revenue.
- Order Processing and Fulfillment: Efficiently managing and fulfilling customer orders ensures timely delivery of products and services, directly impacting customer trust and loyalty.
- Inventory Management: Maintaining optimal stock levels and managing inventory accuracy is crucial for smooth operations and meeting customer demands.
- Financial Management: Accurate financial record-keeping, payroll, and invoicing processes are essential for financial stability and regulatory compliance.
- IT Service Management: Ensuring the delivery of reliable and timely IT services to clients is central to Xymbolic's core business.
IDENTIFY CRITICAL IT SYSTEMS
- Customer Relationship Management (CRM) System: This system manages customer data, sales leads, and support interactions.
- Enterprise Resource Planning (ERP) System: The ERP system streamlines various business processes, including order management, inventory control, and financial accounting (using ODOO Vol. 16)
- Inventory and Stock Management Software: This software tracks stock levels, reordering, and replenishment processes.
- E-commerce Platform: The e-commerce platform enables online sales and transactions.
- Financial Management Software: This system handles accounting, payroll, and financial reporting.
- Communication and Collaboration Tools: These tools facilitate internal and external communication and teamwork.
IDENTIFY CRITICAL RESOURCES
- Employees: The skills and expertise of employees are critical for the smooth functioning of the organization.
- IT Infrastructure: The physical and virtual infrastructure, including servers, networking equipment, and data centers, is essential for delivering IT services.
- Inventory: Maintaining an adequate stock of products is crucial for meeting customer demands.
- Data and Information: Customer data, financial records, and intellectual property are valuable assets that need protection.
DETERMINE POTENTIAL IMPACT OF DISRUPTIONS
- Loss of IT Systems: Downtime or data loss in critical IT systems can disrupt customer service, order processing, and inventory management, leading to revenue loss and customer dissatisfaction.
- Supply Chain Disruptions: Disruptions in the supply chain can result in delays in product availability and affect the ability to fulfill customer orders on time.
- Physical Damage or Loss: Natural disasters or accidents can damage facilities, inventory, and IT infrastructure, causing operational disruptions and financial losses.
- Cyber-security Breaches: Cyber-attacks can compromise customer data, damage reputation, and result in potential legal and financial liabilities.
QUANTIFY FINANCIAL AND OPERATIONAL CONSEQUENCES
- Revenue Loss: Calculate potential revenue loss per day or hour of downtime in critical processes.
- Cost of Recovery: Estimate the cost of restoring IT systems, repairing physical damage, and implementing recovery measures.
- Customer Loss: Assess the potential loss of customers due to prolonged disruptions.
- Penalties and Fines: Consider potential regulatory penalties or legal liabilities resulting from non-compliance or data breaches.
- Operational Delays: Measure the impact of delays in order processing, inventory management, and service delivery.
By conducting this comprehensive BIA, Xymbolic IT Solution Provider Inc can gain valuable insights into its critical processes, IT systems, and resources, enabling the development of a robust and tailored BCP to address potential disruptions effectively.
By identifying and
assessing these potential risks, Xymbolic IT Solution Provider Inc
can develop mitigation strategies and a resilient Business Continuity
Plan (BCP) to ensure preparedness and response in the event of any
disruptive incidents in Olongapo City and Pasig City. This proactive
approach will help protect the company's reputation, customer
satisfaction, and overall business continuity.
NATURAL DISASTERS
Earthquakes: Both Olongapo City and Pasig City are susceptible to earthquakes, which can cause physical damage to facilities, IT infrastructure, and inventory.
Typhoons and Flooding: These natural disasters can lead to property damage, disruptions in transportation, and power outages.
CYBER THREATS
Malware and Ransomware: Cyber-attacks such as malware infections and ransomware can compromise sensitive data, disrupt IT systems, and result in financial losses.
Phishing Attacks: Employees may fall victim to phishing emails, leading to data breaches and unauthorized access to systems.
Distributed Denial of Service (DDoS) Attacks: DDoS attacks can overload the company's servers, causing service outages and customer inconvenience.
POWER OUTAGES
Power Grid Failures: Unplanned power outages can disrupt business operations and impact IT infrastructure, leading to service disruptions.
HUMAN ERROR
Employee Mistakes: Human errors in data entry, inventory management, or customer service may lead to operational inefficiencies and customer dissatisfaction.
Accidental Data Deletion: Employees may accidentally delete critical data, resulting in data loss and potential downtime.
SUPPLY CHAIN DISRUPTIONS
Employee Mistakes: Human errors in data entry, inventory management, or customer service may lead to operational inefficiencies and customer dissatisfaction.
Accidental Data Deletion: Employees may accidentally delete critical data, resulting in data loss and potential downtime.
PHYSICAL SECURITY INCIDENTS
Break-ins and Theft: Security breaches at physical locations can lead to stolen inventory and damage to facilities.
Vandalism: Acts of vandalism can disrupt operations and cause damage to equipment and infrastructure.
FIRE INCIDENTS
Fire Hazards: Fires in facilities or data centers can cause significant damage to assets and result in data loss.
HEALTH AND PANDEMIC RISKS
Disease Outbreaks: Pandemics or severe health risks can impact workforce availability, supply chains, and customer interactions.
REGULATORY COMPLIANCE
Non-Compliance Penalties: Failure to adhere to relevant industry regulations or data protection laws may result in financial penalties and reputation damage.
IT SYSTEMS FAILURES
Hardware Failures: Critical hardware failures can lead to service disruptions and data loss.
Software Glitches: Software bugs or errors may impact the functionality of key IT systems.
By adopting these strategies and approaches, Xymbolic IT Solution Provider Inc. can effectively mitigate risks, ensure business continuity, and provide uninterrupted IT services to its customers in Olongapo City and Pasig City. The company's commitment to preparedness and resilience will reinforce its position as the premier IT solution provider, even in the face of potential disruptions.
Strategies and Approaches for Risk Mitigation and Business Continuity:
REDUNDANCY IN IT SYSTEMS
Xymbolic IT Solution Provider Inc. will implement redundant IT systems, such as servers, networking equipment, and power sources, at both the Olongapo City and Pasig City locations. Redundancy will ensure that if one system fails, the backup system seamlessly takes over, minimizing downtime.
DATA BACKUPS AND DISASTER RECOVERY
Regular and automated data backups will be performed to secure critical customer data, financial records, and business information. The backups will be stored in secure offsite locations to safeguard against data loss in case of disasters or cyber incidents. A comprehensive disaster recovery plan will be in place to facilitate rapid data restoration.
CLOUD SERVICES ADOPTION
Regular and automated data backups will be performed to secure critical customer data, financial records, and business information. The backups will be stored in secure offsite locations to safeguard against data loss in case of disasters or cyber incidents. A comprehensive disaster recovery plan will be in place to facilitate rapid data restoration.
REMOTE WORK ARRANGEMENTS
Xymbolic will establish a robust remote work policy and infrastructure to enable employees to work from home or alternate locations during emergencies, such as pandemics or adverse weather conditions. This ensures the continuity of essential operations even when physical offices are inaccessible.
PARTNERSHIPS WITH ALTERNATIVE VENDORS
Xymbolic will establish strategic partnerships with alternative vendors for key products and services. This diversification reduces reliance on a single vendor and ensures a continuous supply chain even if one vendor faces disruptions.
BUSINESS CONTINUITY TRAINING AND DRILLS
Xymbolic will establish strategic partnerships with alternative vendors for key products and services. This diversification reduces reliance on a single vendor and ensures a continuous supply chain even if one vendor faces disruptions.
PHYSICAL SECURITY MEASURES
Enhanced physical security measures will be implemented at both locations to protect facilities, inventory, and critical equipment from theft, vandalism, or unauthorized access.
CYBER-SECURITY MEASURES
Robust cyber-security measures, including firewalls, intrusion detection systems, and employee awareness training, will be adopted to protect against cyber threats like malware, ransomware, and phishing attacks.
SUPPLY CHAIN MANAGEMENT
Xymbolic will actively monitor and assess its supply chain to identify potential vulnerabilities and disruptions. Developing contingency plans and building relationships with reliable suppliers will be a priority.
INCIDENT RESPONSE TEAM
A dedicated incident response team will be established with clearly defined roles and responsibilities. This team will be responsible for promptly addressing and managing any disruptions or incidents that occur.
CONTINUOUS MONITORING AND EVALUATION
A dedicated incident response team will be established with clearly defined roles and responsibilities. This team will be responsible for promptly addressing and managing any disruptions or incidents that occur.
By following this Incident Response Plan, Xymbolic IT Solution Provider Inc can effectively manage incidents and disasters at both the Olongapo City and Pasig City branches, minimizing their impact and ensuring a swift recovery process. The clear roles, communication channels, and escalation process will enable a coordinated and efficient response across the organization.
STEP 1: INCIDENT IDENTIFICATION AND REPORTING
Employees at both the Olongapo City and Pasig City branches are trained to identify and promptly report any incidents or disasters to the Incident Response Team (IRT). Incidents can include cyberattacks, physical security breaches, natural disasters, or any other disruptive events.
STEP 2: INCIDENT RESPONSE TEAM ACTIVATION
The Incident Response Team will be activated immediately upon receiving the incident report. The team will consist of key personnel with specific roles and responsibilities.
STEP 3: INCIDENT ASSESSMENT AND CLASSIFICATION
The Incident Response Team will be activated immediately upon receiving the incident report. The team will consist of key personnel with specific roles and responsibilities.
STEP 4: INCIDENT CONTAINMENT AND MITIGATION
The IRT will take immediate action to contain and mitigate the incident's effects. This may involve isolating affected systems, initiating data backups, activating disaster recovery measures, and applying cybersecurity protocols.
STEP 5: COMMUNICATION AND NOTIFICATION
The IRT will take immediate action to contain and mitigate the incident's effects. This may involve isolating affected systems, initiating data backups, activating disaster recovery measures, and applying cybersecurity protocols.
STEP 6: ESCALATION PROCESS
Low Severity Incidents: Incident Response Team handles the incident internally, and relevant departments are notified for support if required. (Supervisory Level)
Medium Severity Incidents: Incident Response Team escalates the incident to senior management for further decision-making and resource allocation. (Managerial/ ManCom Level)
High Severity Incidents: Incident Response Team immediately notifies executive management and senior leaders to make critical decisions. (ExeCom Level)
STEP 7: INCIDENT RESOLUTION AND RECOVERY
The IRT continues to work on resolving the incident, restoring affected services, and recovering data and operations. Regular updates are provided to stakeholders throughout the process.
STEP 8: POST-INCIDENT ANALYSIS AND REPORTING
After the incident is resolved, the IRT conducts a thorough post-incident analysis to identify root causes and lessons learned. A detailed report is prepared for management and relevant stakeholders.
INCIDENT RESPONSE TEAM ROLES AND COMMUNICATION CHANNELS
Incident Response Team Lead: Coordinates the overall response effort, directs actions, and communicates with executive management.
IT Security Manager: Oversees the technical aspects of the response, such as cyber-security measures and data protection.
Operations Manager: Coordinates the restoration of business operations and ensures continuity.
Communications Manager: Handles external and internal communication, media relations, and customer notifications.
IT Support Representatives: Provides technical support and assists in implementing recovery measures.
HR Representative: Manages employee communications, welfare, and any workforce-related issues.
COMMUNICATION CHANNELS
Incident Response Team members communicate through secure channels like encrypted messaging platforms or phone calls.
External communication to customers, vendors, regulatory authorities, and media will be handled through designated spokespersons and official communication channels (e.g., email, website, press releases).
RECOVERY STRATEGIES AND ACTIONS FOR XYMBOLIC IT SOLUTIONS PROVIDER CORPORATION
By implementing these recovery strategies and actions, Xymbolic IT Solution Provider Inc can ensure the swift recovery of critical IT systems, infrastructure, and operations in the event of an incident, minimizing downtime, and maintaining seamless service delivery to customers in Olongapo City and Pasig City.
DATA BACKUP AND RECOVERY
Strategy: Regularly back up all critical data, including customer information, financial records, and essential business documents, both onsite and in secure offsite locations or the cloud.
Action: Upon identifying an incident, the Incident Response Team (IRT) will immediately initiate data restoration from the most recent backups to ensure minimal data loss.
BACKUP SITE ACTIVATION
Strategy: Establish a backup site or alternate location that mirrors critical IT systems and infrastructure to ensure redundancy.
Action: In the event of a severe incident affecting the main locations, the IRT will activate the backup site and redirect services to maintain continuity.
SYSTEM REDUNDANCY AND FAILOVER
Strategy: Implement redundancy for critical IT systems, such as servers, networking equipment, and power sources, to ensure seamless failover in case of system failures.
Action: The IRT will configure failover mechanisms to automatically switch to backup systems when the primary systems experience disruptions.
DISASTER RECOVERY PLAN EXECUTION
Strategy: Develop a comprehensive Disaster Recovery Plan (DRP) that outlines step-by-step procedures for recovering critical systems and services.
Action: The IRT will follow the DRP to systematically restore IT systems, infrastructure, and essential services, ensuring a structured and efficient recovery process
VENDOR AND SUPPLIER SUPPORT
Strategy: Establish partnerships with vendors and suppliers who can provide emergency support and resources during a crisis.
Action: The IRT will engage with designated vendors to expedite hardware repairs or replacements and access additional resources if necessary.
IT SERVICE MANAGEMENT RESTORATION
Strategy: Ensure the continuity of IT service management processes to address customer inquiries, support requests, and incident management.
Action: The IRT will prioritize the restoration of IT service management tools and communication channels to maintain seamless customer support.
COMMUNICATION INFRASTRUCTURE RECOVERY
Strategy: Establish redundant communication channels to ensure continuous internal and external communication during an incident.
Action: The IRT will promptly restore communication infrastructure, including email services, phone lines, and messaging platforms, to facilitate coordinated efforts.
TESTING AND VALIDATION
Strategy: Regularly test and validate the effectiveness of the recovery strategies and plans through simulated exercises and drills.
Action: The IRT will conduct scheduled testing to verify the successful recovery of critical IT systems, infrastructure, and operations.
EMPLOYEE TRAINING AND AWARENESS
Strategy: Educate employees about the recovery procedures and their roles during a crisis to enhance preparedness.
Action: The IRT will conduct training sessions and workshops to ensure employees are familiar with the recovery actions they need to take.
CONTINUOUS IMPROVEMENT AND DOCUMENTATION
Strategy: Continuously review and update the recovery strategies and plans based on lessons learned from real incidents and exercises.
Action: The IRT will document the details of the recovery actions taken during incidents and incorporate the insights into the overall recovery strategy.
A well-defined communication strategy is vital to keep all stakeholders informed, manage their expectations, and maintain transparency during a crisis. Effective communication will instill confidence in Xymbolic IT Solution Provider Corp. ability to manage the situation. Assigning specific individuals to communication roles ensures a coordinated and consistent approach. Here is the communication strategy and the designated communication responsibilities:
INCIDENT RESPONSE TEAM (IRT) SPOKESPERSON
Responsibility: The IRT Spokesperson is the official representative of Xymbolic during the crisis. This individual will provide updates to the media, coordinate press releases, and address public inquiries.
INTERNAL COMMUNICATION MANAGER
Responsibility: The Internal Communications Manager is responsible for keeping employees informed about the situation, updates on recovery efforts, and guidance on their roles during the crisis.
CUSTOMER RELATIONS REPRESENTATIVE
Responsibility: The Internal Communications Manager is responsible for keeping employees informed about the situation, updates on recovery efforts, and guidance on their roles during the crisis.
VENDOR AND SUPPLIER LIAISON
Responsibility: The Vendor and Supplier Liaison will maintain communication with critical vendors and suppliers, keeping them informed about the situation, recovery progress, and potential impacts on the supply chain.
REGULATORY AFFAIRS MANAGER
Responsibility: The Regulatory Affairs Manager will handle communication with relevant regulatory authorities, ensuring compliance reporting and providing necessary information as required by law.
COMMUNICATION CHANNELS
Crisis Communication Center: Establish a central communication center to monitor and coordinate all communication efforts during the crisis. This center will serve as the primary point of contact for all communication activities.
Internal Communication Channels: Utilize company-wide emails, intranet portals, and team meetings to update employees on the situation, response efforts, and any changes to work arrangements.
Customer Communication Channels: Send email notifications, personalized messages, and updates on the company website to inform clients about the incident, its impact on services, and the steps being taken to address the situation.
Vendor and Supplier Communication Channels: Engage with vendors and suppliers through direct communication channels, including emails, phone calls, and web portals, to maintain transparency and collaboration.
Media and Public Relations: The IRT Spokesperson will liaise with media outlets and conduct press briefings as needed. All official statements and press releases will be carefully crafted to ensure accurate and consistent messaging.
Social Media Platforms: Utilize official social media channels to provide updates to the public and respond to inquiries, while maintaining a consistent tone and message.
KEY MESSAGING
Acknowledge the Incident: Communicate openly about the incident, acknowledging its occurrence, and the company's commitment to addressing it promptly.
Regular Updates: Provide timely and regular updates on the situation, recovery efforts, and progress toward resolution to all stakeholders.
Transparency: Be transparent about the extent of the impact and the steps being taken to minimize disruptions and restore normal operations.
Assurance of Support: Reassure stakeholders of Xymbolic's commitment to supporting them throughout the crisis and working towards a swift resolution.
Contact Information: Provide clear contact information for stakeholders to reach out with any questions or concerns.
By adhering to this communication strategy and assigning specific individuals to handle communication responsibilities, Xymbolic IT Solution Provider Inc can effectively manage communications during a crisis and foster trust among employees, clients, vendors, regulatory authorities, and the media in Olongapo City and Pasig City.
To ensure that all employees are aware of the Business Continuity Plan (BCP) of Xymbolic IT Solution Provider Inc. and their roles during an incident, the company should implement a comprehensive awareness and training program. This program should include the following steps:
BCP DOCUMENTATION AND ACCESSIBILITY
Ensure that the BCP is well-documented, easily accessible, and available to all employees. Make it available both physically (e.g., printed copies) and digitally (e.g., on the company intranet).
BCP OVERVIEW AND INTRODUCTION
Conduct an introductory session to familiarize employees with the BCP's purpose, importance, and how it relates to the company's overall mission and resilience.
BCP TRAINING SESSIONS
Organize regular training sessions focused on the BCP, its components, and the specific roles and responsibilities of employees during different incidents.
ROLE-SPECIFICE TRAINING
Tailor training sessions to address the unique roles and tasks of different departments and employees. Ensure that employees understand how their actions contribute to the overall continuity efforts.
TABLETOP DRILLS AND SIMULATIONS
Conduct tabletop drills and simulations regularly to allow employees to practice implementing the BCP in a controlled environment. These exercises help reinforce knowledge and build confidence.
REALISTIC SCENARIO EXERCISES
Periodically organize more comprehensive exercises involving various teams and departments to simulate real-life crisis scenarios. These exercises should test response times, decision-making, and coordination.
POST-EXERCISE EVALUATIONS AND FEEDBACK
After each training session or drill, conduct evaluations to gather feedback from participants. Use this feedback to identify areas for improvement and refine the BCP accordingly.
BCP REFRESHER COURSES
Provide refresher courses on the BCP and its updates regularly, especially when there are significant changes to the plan or the organization's operations.
INCORPORATE BCP INTO OBOARDING PROCESS
Introduce the BCP as part of the onboarding process for new employees, ensuring that they understand their roles and responsibilities from the beginning.
EMPLOYEE COMMUNICATION CHANNELS
Maintain open communication channels to address employee questions, concerns, and suggestions related to the BCP. Encourage feedback and involvement.
RECOGNITION AND INCENTIVES
Acknowledge and reward employees who demonstrate exemplary adherence to the BCP and exhibit proactive preparedness during training and drills.
CONTINUOUS IMPROVEMENT AND UPDATES
Regularly review and update the BCP based on feedback, lessons learned from real incidents, and industry best practices.
By consistently conducting training sessions, drills, and exercises, Xymbolic IT Solution Provider Inc. can cultivate a culture of preparedness and resilience among its employees. This proactive approach will ensure that all staff members are well-prepared to effectively implement the BCP during incidents, minimizing the impact on business operations in Olongapo City and Pasig City.
Regularly testing the Business Continuity Plan (BCP) through simulated scenarios is essential to ensure its effectiveness and identify areas for improvement. Here's a step-by-step guide on how Xymbolic IT Solution Provider Inc. can perform these tests and update the plan accordingly:
Design Test Scenarios: Develop a range of simulated scenarios that could potentially impact the organization, such as cyberattacks, natural disasters, power outages, or supply chain disruptions. Each scenario should be carefully designed to test specific aspects of the BCP.
Establish Objectives: Define clear objectives for each test scenario, outlining what the organization aims to achieve and the specific areas to be evaluated.
Select Participants: Identify individuals or teams who will participate in the simulation exercises. Involve representatives from various departments to ensure a comprehensive assessment.
Communicate the Exercise: Inform all relevant employees about the upcoming simulation exercises, providing the date, time, objectives, and expected outcomes. Communicate that it is a practice exercise and not an actual incident.
Conduct the Simulation: Run the simulation exercises, replicating the selected scenarios as realistically as possible. Encourage participants to respond as they would in a real crisis.
Evaluate Performance: After each simulation, conduct a thorough evaluation of the participant’s responses and actions. Identify strengths, weaknesses, and areas requiring improvement.
Collect Feedback: Gather feedback from participants to gain insights into their experiences, challenges faced, and suggestions for improvement.
Identify Lessons Learned: Analyze the results of the simulation exercises to identify valuable lessons learned. Pinpoint areas where the BCP performed well and areas that need enhancement.
Update the BCP: Based on the feedback and lessons learned, revise the BCP to address identified weaknesses and enhance its effectiveness. Update contact information, roles, responsibilities, and any procedural changes.
Document Changes: Ensure all modifications to the BCP are documented thoroughly, and the updated version is accessible to all relevant stakeholders.
Training and Awareness: Communicate the changes and improvements made to the BCP to all employees. Conduct refresher training sessions if necessary to ensure everyone is familiar with the updates.
Schedule Regular Reviews: Establish a schedule for periodic reviews of the BCP, considering industry trends, regulatory changes, and organizational developments. This ensures that the plan remains up-to-date and relevant.
Involve Leadership: Engage executive management in the review process to gain their support and ensure the BCP aligns with the company's strategic objectives.
Seek External Feedback: Consider engaging external experts or consultants to review the BCP and provide an objective assessment.
Test Diverse Scenarios: Periodically introduce new and diverse scenarios in simulation exercises to challenge the BCP and evaluate its adaptability.
By following this approach, Xymbolic IT Solution Provider Inc. can continuously improve its BCP, ensuring it effectively addresses potential incidents and maintains business continuity in Olongapo City and Pasig City. Regular testing and updates will reinforce the company's preparedness and ability to navigate various disruptions.
Assessing the business continuity capabilities of critical vendors and suppliers is crucial to identifying potential vulnerabilities in the supply chain and mitigating risks. Here's a step-by-step guide to assess and establish alternate arrangements and partnerships:
IDENTIFY CRITICAL VENDORS AND SUPPLIERS
Identify vendors and suppliers whose products or services are essential for Xymbolic IT Solution Provider Inc's operations. These may include hardware suppliers, software providers, logistics partners, and key service providers.
CONDUCT A BUSINESS CONTINUITY QUESTIONNAIRE
Develop a questionnaire to assess the business continuity and disaster recovery capabilities of the identified vendors and suppliers. The questionnaire should inquire about their BCP, risk management practices, and recovery plans.
REVIEW VENDOR CONTRACTS
Review existing contracts with critical vendors to understand the terms related to business continuity, disaster recovery, and contingency plans.
REQUEST BUSINESS CONTINUITY PLANS
Request copies of the BCPs from critical vendors and suppliers. Evaluate the plans to ensure they meet Xymbolic's standards and align with the company's own BCP requirements.
EVALUATE VENDOR BCP EFFECTIVENESS
Assess the effectiveness and feasibility of each vendor's BCP. Look for evidence of regular testing, training, and proactive measures to ensure business continuity.
IDENTIFY SINGLE POINTS OF FAILURE
Identify any single points of failure within the supply chain where reliance on a single vendor poses significant risks. Consider establishing alternative arrangements for such scenarios.
ESTABLISH COMMUNICATION CHANNELS
Establish clear communication channels with critical vendors and suppliers to ensure open dialogue during a crisis or potential disruptions.
DEVELOP ALTERNATIVE VENDOR PARTNERSHIPS
Identify and establish partnerships with alternative vendors and suppliers who can provide similar products or services. These partnerships serve as backup options in case of disruptions from primary vendors.
CONTRACTUAL CLAUSES FOR BCP COMPLIANCE
Incorporate contractual clauses in vendor agreements that mandate compliance with BCP requirements. Specify expectations for business continuity planning and disaster recovery efforts.
PERIODIC VENDOR AUDITS
Conduct periodic audits of critical vendors and suppliers to assess their ongoing compliance with BCP requirements and risk management practices.
SUPPLIER PERFORMANCE EVALUATIONS
Evaluate supplier performance regularly to ensure they meet service level agreements and adhere to BCP commitments.
DEVELOP CONTINGENCY PLANS
Develop contingency plans that outline specific steps to be taken if a critical vendor or supplier experiences disruptions. This includes activating alternative arrangements and partnerships.
MONITOR INDUSTRY TRENDS
Stay informed about industry trends, regulatory changes, and market conditions that may impact critical vendors and suppliers. Adjust strategies accordingly.
COLLABORATE WITH VENDORS
Work collaboratively with critical vendors and suppliers to strengthen their business continuity capabilities, fostering a mutually beneficial partnership.
By following these steps, Xymbolic IT Solution Provider Inc can effectively assess and enhance the business continuity capabilities of critical vendors and suppliers. Establishing alternate arrangements and partnerships ensures a resilient supply chain, reducing the risk of severe disruptions to the company's operations in Olongapo City and Pasig City.
To ensure that the Business Continuity Plan (BCP) of Xymbolic IT Solution Provider Inc aligns with relevant legal and regulatory requirements in Olongapo City and Pasig City, the company should follow these steps:
CONDUCT A REGULATORY COMPLIANCE REVIEW
Identify the relevant laws, regulations, and industry standards related to business continuity and disaster recovery in Olongapo City and Pasig City. These may include local, regional, or national regulations governing business operations and data protection.
ENGAGE LEGAL AND COMPLIANCE EXPERTS
Involve legal and compliance experts, either internal or external, who are well-versed in the specific regulations applicable to Xymbolic's operations. Seek their guidance to ensure the BCP meets the required standards.
IDENTIFY BCP COMLIANCE GAPS
Review the BCP to identify any gaps or inconsistencies with the legal and regulatory requirements. Ensure that the plan addresses each relevant aspect comprehensively.
INCORPORATE REGULATORY REQUIREMENTS INTO THE BCP
Revise the BCP to explicitly incorporate the specific legal and regulatory requirements that apply to Xymbolic IT Solution Provider Inc. Ensure that the plan includes all necessary elements to comply with these requirements.
DATA PRIVACY AND PROTECTION COMPLIANCE
If the BCP involves handling customer data or personal information, ensure compliance with data privacy and protection regulations in Olongapo City and Pasig City. Implement measures to safeguard sensitive data during a crisis.
VENDOR AND SUPPLIER COMPLIANCE
Verify that critical vendors and suppliers involved in the BCP also comply with applicable legal and regulatory requirements. Require them to provide evidence of their compliance.
EMPLOYEE TRAINING ON REGULATORY COMPLIANCE
Educate employees about the relevant legal and regulatory requirements that pertain to their roles within the BCP. Ensure they understand their responsibilities in maintaining compliance during an incident.
AUDIT AND MONITORING
Regularly audit and monitor the implementation of the BCP to ensure ongoing compliance with legal and regulatory requirements. Update the plan as needed to reflect any changes in the regulatory landscape.
REPORTING AND DOCUMENTATION
Maintain accurate and up-to-date records of the BCP, including any modifications made to ensure compliance. Keep records of training sessions, audits, and regulatory reviews.
SEEK LEGAL ADVICE
When uncertain about how to address specific legal requirements within the BCP, seek legal advice to ensure accurate interpretation and implementation.
COLLABORATE WITH REGULATORS
Engage with relevant regulatory authorities in Olongapo City and Pasig City to gain insights into their expectations regarding business continuity and disaster recovery.
By integrating relevant legal and regulatory requirements into the BCP, Xymbolic IT Solution Provider Inc can demonstrate its commitment to compliance and enhance its readiness to face potential incidents. This approach ensures that the BCP aligns with the local legal framework, safeguarding the company's reputation, and helping it meet its obligations in Olongapo City and Pasig City.
Allocating appropriate resources and budget for the implementation and maintenance of the Business Continuity Plan (BCP) is essential to ensure its effectiveness and sustainability. Here are the key steps to allocate resources and budget for the BCP:
CONDUCT A BUSINESS IMPACT ANALYSIS
Start by conducting a thorough Business Impact Analysis to identify critical business processes, IT systems, and resources. This analysis will help prioritize areas that require additional resources and budget allocation.
IDENTIFY BCP IMPLEMENTATION REQUIREMENTS
Based on the BIA results, identify the specific requirements for implementing the BCP. This may include hardware and software upgrades, data backup solutions, alternative work arrangements, training, and more.
CREATE A DETAILED BCP IMPLEMENTATION PLAN
Develop a comprehensive implementation plan that outlines the tasks, timelines, responsibilities, and resources required for each aspect of the BCP. This plan will serve as a road-map for the allocation of resources.
ESTIMATE COSTS
Work with relevant stakeholders to estimate the costs associated with each component of the BCP implementation plan. Consider both one-time expenses and ongoing costs for maintenance.
PRIORITIZE RESOURCE ALLOCATION
Prioritize resource allocation based on the criticality of business processes and the potential impact of disruptions. Allocate more resources to areas with higher priority and significant risk.
SECURE MANAGEMENT SUPPORT
Gain support from executive management and key decision-makers to ensure sufficient budget allocation for the BCP. Present the BIA results and highlight the importance of business continuity to the organization's success.
BUDGET FOR TRAINING AND AWARENESS
Allocate budget for training sessions, awareness campaigns, and drills to educate employees about the BCP and their roles during incidents. An informed workforce is vital to the plan's success.
ALLOCATE IT BUDGET FOR TECHNOLOGY UPGRADES
Set aside a portion of the IT budget for technology upgrades that enhance the resilience of critical IT systems, such as redundant hardware, data backups, and cloud services.
CONSIDER INSURANCE COVERAGE
Assess whether additional insurance coverage for business interruption or disaster recovery is necessary and include it in the budget if applicable.
REGULAR MAINTENANCE BUDGET
Allocate a separate budget for ongoing maintenance and updates to the BCP. Regular reviews, tests, and improvements are essential for the plan's continued effectiveness.
REEVALUATE AND ADJUST
Regularly review the budget allocation for the BCP to ensure it remains aligned with the organization's changing needs and priorities. Make adjustments as necessary.
MONITOR RESOURCE UTILIZATION
Monitor resource utilization during the BCP implementation and maintenance phases. Optimize resource allocation to maximize efficiency and cost-effectiveness.
By allocating appropriate resources and budget for the BCP, Xymbolic IT Solution Provider Inc can enhance its preparedness and resilience, minimizing the impact of potential incidents and ensuring the continuity of operations in Olongapo City and Pasig City.
To effectively execute the Business Continuity Plan (BCP) of Xymbolic IT Solution Provider Inc, the following supporting documents, contact lists, procedures, and technical details are necessary:
SUPPORTING DOCUMENTS
Business Impact Analysis (BIA) Report: Provides an overview of critical business processes, IT systems, and resources, along with their potential impact on the organization in case of disruptions.
Risk Assessment Report: Identifies potential risks, vulnerabilities, and threats that could affect business continuity, along with their likelihood and potential consequences.
BCP Policy Document: Outlines the purpose, scope, objectives, and general guidelines for developing and implementing the BCP.
BCP Roles and Responsibilities: Clearly defines the roles and responsibilities of key personnel involved in executing the BCP during incidents.
Incident Response Team (IRT) Charter: Describes the formation, composition, and responsibilities of the Incident Response Team.
Communication Plan: Details the communication strategies, channels, and contact information for internal and external stakeholders during incidents.
CONTACT LISTS
Incident Response Team (IRT) Contact List: Includes contact information for all members of the IRT, including names, roles, phone numbers, and email addresses.
Employee Contact List: Contains the contact details of all employees, their designated communication channels, and emergency contact information.
Critical Vendor and Supplier Contact List: Provides contact information for critical vendors and suppliers, including their designated points of contact.
PROCEDURE AND GUIDELINES
Emergency Evacuation Procedures: Outlines the procedures for evacuating employees and visitors from the premises during emergencies.
Data Backup and Recovery Procedures:Details the process of backing up critical data and the steps to restore it in case of data loss.
IT System Recovery Procedures: Provides step-by-step guidelines for recovering critical IT systems, infrastructure, and applications.
Alternative Work Arrangements: Describes the procedures for implementing remote work arrangements during incidents that prevent access to physical offices.
Supply Chain Management Procedures: Outlines the procedures for engaging with critical vendors and suppliers during disruptions and activating alternate arrangements if necessary.
TECHNICAL DETAILS
Network Diagrams and Infrastructure Details: Provides technical diagrams and documentation of the organization's network topology, data centers, servers, and other critical IT infrastructure.
Software and Hardware Inventory: Lists all software applications and hardware devices utilized by the organization, including versions and specifications.
Data Center and Cloud Services Information: Includes details about the data center locations, cloud service providers, and contractual arrangements for critical IT services.
Having these
supporting documents, contact lists, procedures, and technical
details readily available and up-to-date will facilitate the smooth
execution of the BCP during incidents.
Other Security Partners
We are in good company.




